With tools like LocateMyLaptop and LoJack for Laptops, law enforcement can identify the location of your stolen laptop within an address range. At that point, it may become necessary to obtain a warrant for several location wherein the DHCP range might be in use. By the time a warrant is procured, your laptop (or other protected network asset) may have been moved without leaving a trace.
If your laptop smelled like drugs, Law Enforcement could use drug-sniffing dogs to scour the area and would have probable cause to search within spaces identified by K-9 units.
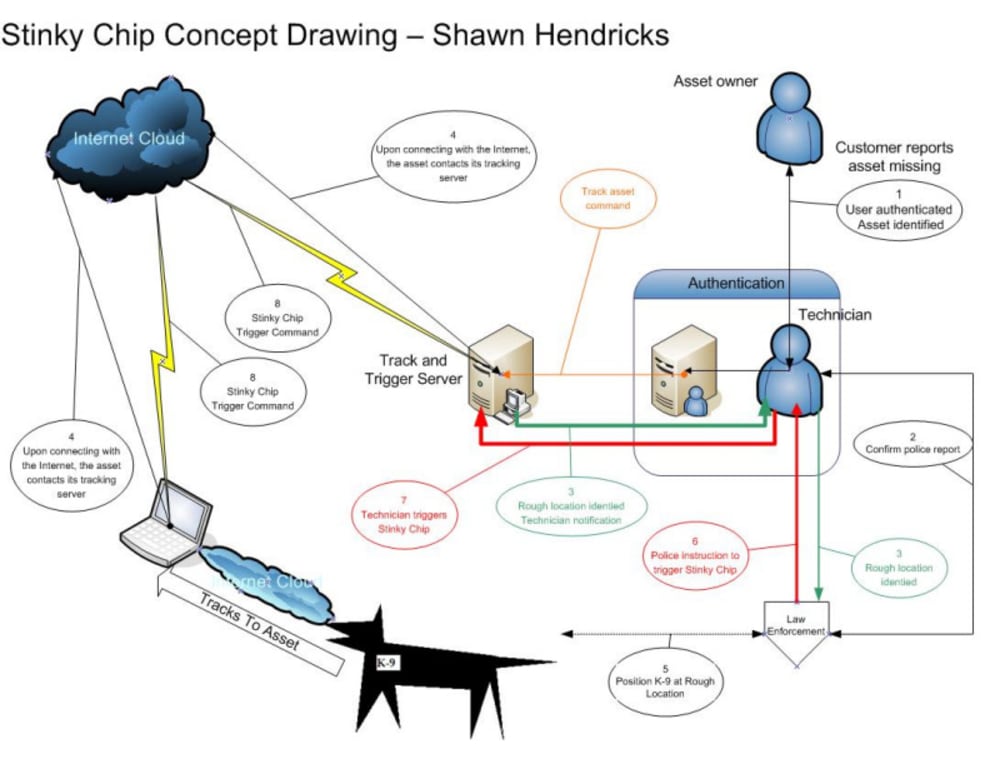
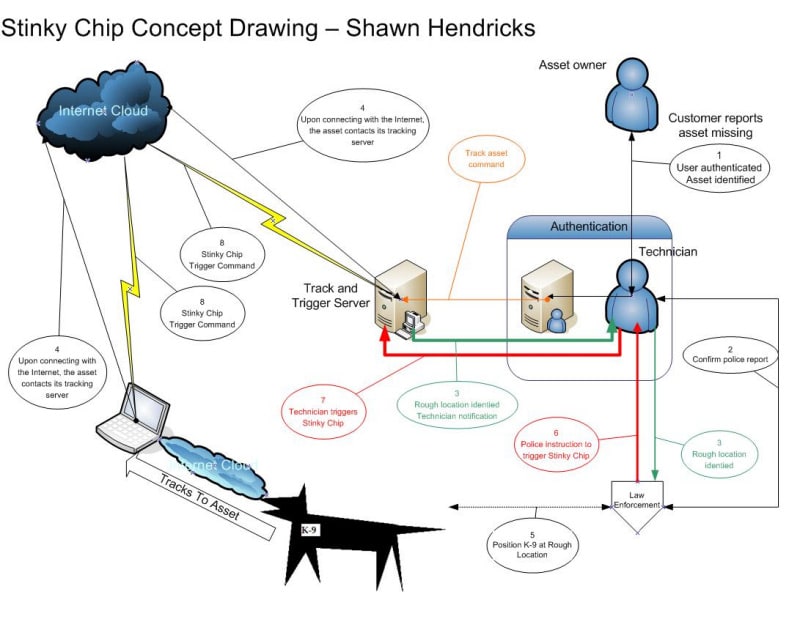
A Stinky Chip works in concert with one of the Internet location services and law enforcement to precisely pinpoint the location of a stolen piece of equipment connected that has been re-connected to the Internet. The Stinky Chip is remotely triggered by technicians at a headquarters location to open or expose its scent-carrying payload. Accidental Stinky Chip triggering can be prevented by protecting the triggering mechanism using any of a number of identificaiton alogrithms.
Stinky Chips can contain scents may be specialized pheremones undetectible by humans, stink that repels humans or training scents commonly in use for training drug dogs. The third option is most viable because dogs trained in locating drugs could be used.
Specially trained dogs could be used with stinky chips armed with non-drug pheremones. Similarly, specialized scent detectors could be used in place of dogs for tailored chemical scent agents.
~~~~
Standard Stinky Chip
After filing a police report for a stolen asset (laptop or other network node device) the following steps are undertaken.
1. Via telephone or the Internet, the asset owner's identity is verified. An official police report is recorded and verified by a technician.
2. The owner's asset is identified by the technician.
3. When the asset is next attached to the Internet, it notifies the tracking and trigger server and requests status. Half-hourly thereafter, the status request is repeated. Normally, the returned notice contains a null value and the procedure ends.
4. The returned value contains notification that the asset has been stolen and standard Internet location techniques are employed to narrow down the asset's location to a "Rough Location."
5. Law Enforcement is notified.
6. Law Enforcement has notifies the Technician when working dog (K-9) units are positioned in the Rough Location of the stolen asset.
7. The Technician triggers the Stinky Chip.
8. Scent released from the Stinky Chip guides Law Enforcement working dogs (K-9 units) to the exact location of the stolen asset.
~~~~
Disconnect Stinky Chip
After disconnecting a nuclear or other sensitive device for a period of time, the Disconnect Stinky Chip triggers automatically with no intervention required.
~~~~
If a crook knows the cops are on the way, it is easy to shut the laptop off. This is why 'dog whistle' alerts may be ineffective. A triggered Stinky Chip, on the other hand, is not affected by removing power.
Like this entry?
-
About the Entrant
- Name:Shawn Hendricks
- Type of entry:individual
- Patent status:none