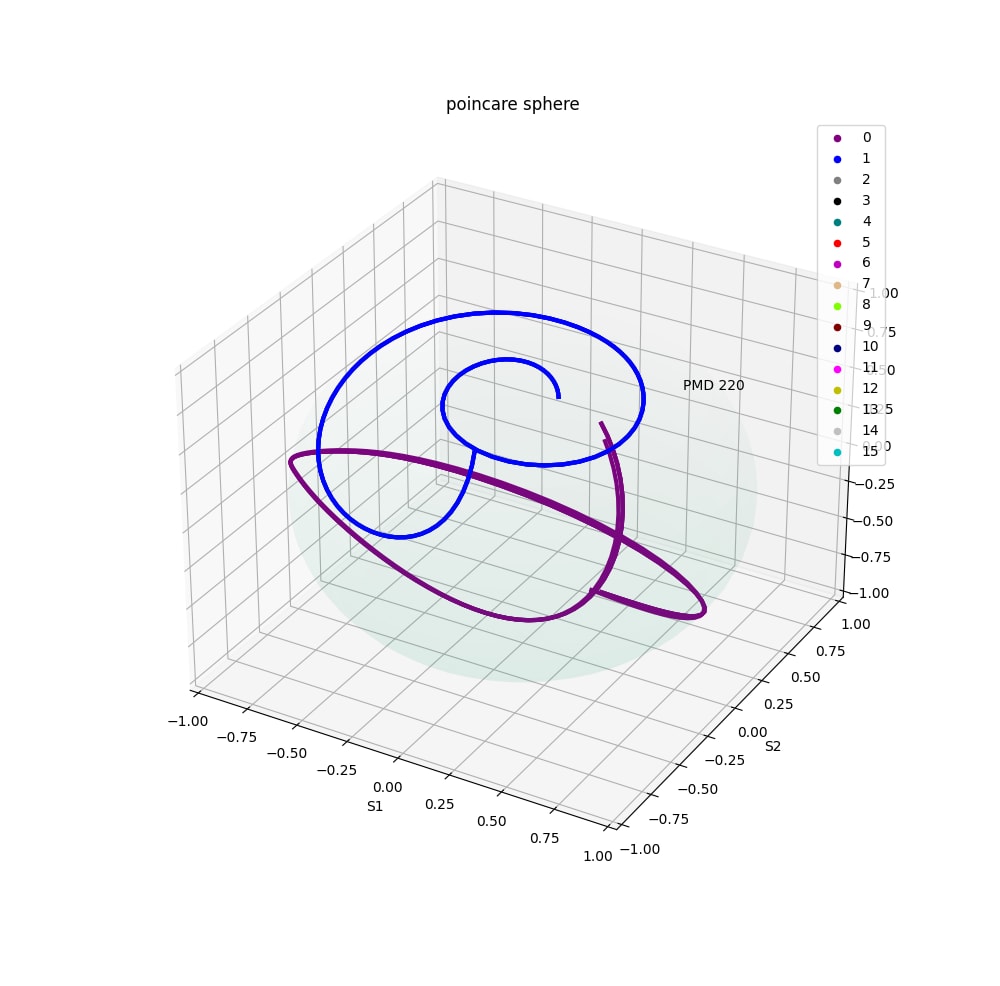
Have you ever seen a wireless signal? Me neither, but Endpoint Security technology sees a naturally occurring fingerprint in every signal. These fingerprints can be seen by us when plotted on the surface of a sphere. They are unique to each device transmitting a signal and are quite stable for IoT devices that are fixed in place, like sensors and actuators in manufacturing environments. As recent news indicates, cyber-attacks on manufacturers and refineries are accelerating. It is time to take action with a proactive solution.
As nation state actors become more active in cyber-attacks on infrastructure, they also become more sophisticated. Rather than shutting down a plant, for instance, they might target product quality, which is harder to detect. To stay out in front of the attackers requires a proactive approach that includes security for wireless edge devices.
Endpoint Security Inc will soon release a Wireless Intrusion Detection System (WIDS) that detects wireless intruders by the signal they send, rather than simply relying upon the data that the signal contains. By using polarization mode dispersion, it is possible to protect the wireless channel (that is, the path from sensor to access point) identifying hostile actors who attempt to imitate authenticated devices to gain entry into a wireless network. ATTACKERS CAN BE IDENTIFIED BEFORE THEY CONNECT.
Today, two prototypes have been built and been subjected to more than 250 tests. The last 75 tests were performed in a controlled manufacturing environment and were designed to stress the prototypes to their limits. The technology proved to be strong and stable. It met the challenge and produced 100% identification of the sensors transmitting wirelessly.
Today, there is no good way to protect older legacy endpoint devices from attack. Wireless devices are particularly vulnerable, including temperature sensors, control valve position sensors and even perimeter security cameras. Attackers spoof these devices to gain access to networks. The United States infrastructure is particularly vulnerable. It is estimated that there are 30 billion installed endpoint devices. Protecting these devices represents a $4.4 billion urgent market.
Any solution that requires a change to the endpoint devices will not work. Industry cannot afford to change every endpoint. The software in some cannot even be changed. Many of these devices have minimal CPU power and only small amounts of memory. Since the weakest link is the point from which an attacker begins, this would leave industry vulnerable.
The impact of employing a solution for use with legacy devices is extremely large. A report from the University of Cambridge and the Lloyd’s of London insurance company estimates a successful attack on U.S. electrical infrastructure could result in a loss of $1 trillion. [Reuters, Technology News, July 8. 2015] The U.S. incurs approximately one hundred thousand attacks a day. [Insurance Journal, Federal Energy Regulator Warns on Cyber Attacks on Power Grid, Ari Natter, March 28, 2018] The likelihood of a successful attack of proportion causes this study to be of some urgency.
Video
-
Awards
-
 2021 Top 100 Entries
2021 Top 100 Entries
Like this entry?
-
About the Entrant
- Name:Page Heller
- Type of entry:teamTeam members:Page Heller, Jay Labhart, Bob Moore
- Software used for this entry:Python, C++
- Patent status:patented