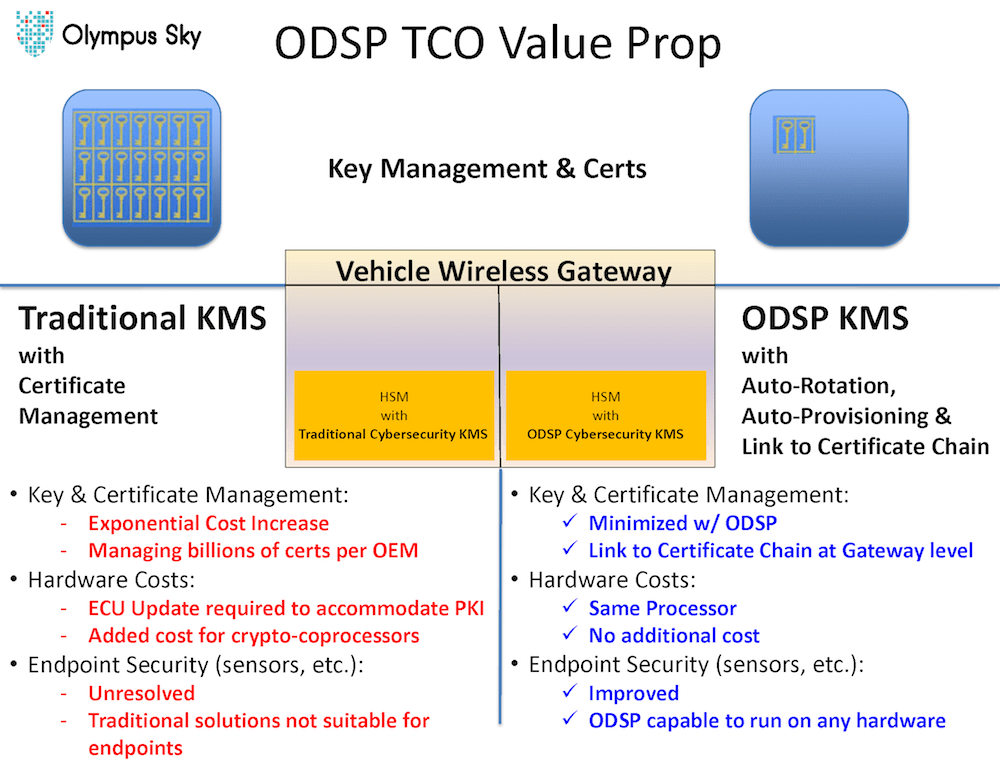
Organically Derived Security Protocol is a zero knowledge key management (ZKKM) solution for securing ECU-to-ECU communication within the connected vehicle and IoT applications; particularly for transmissions between externally exposed, edge ECU sensors connected to ECUs within the connected vehicle infrastructure. Specific benefits include reductions of communication latency, implementation complexity, processing power and energy consumption. Implementation issues discussed include provisioning, key rotation, synchronization, re-synchronization, digital signatures and ZKKM extensions enabling high potential entropy.
ODSP (Organically Derived Security Protocol) is an example of ZKKM and enables tailored key management to work standalone or in conjunction with PKI systems. The software library integrates into IoT Nodes, Gateways, Backend Servers and remote devices. Because an ODSP ZKKM based system acts as a closed system, the provisioning of new and existing devices is included to retrofit exisiting fleets with ODSP ZKKM security. Backend ODSP ZKKM Services also incorporate attack detection and reporting as part of a ODSP ZKKM backend. Thus, allowing backend ZKKM Services to provide policy based automatic re-provisioning and self-healing of a ZKKM solution.
A ZKKM cryptographic solution allows two parties to securely encrypt communication without directly exchanging information that could be used to decrypt the aforementioned communication , while maintaining seed and/or cryptographic keys internally within a secure area on each side of the connection.
Additionally, for added security and obfuscation, keys, seeds, and even cryptographic algorithms, including the bulk encryption algorithm, may be internally rotated on a periodic basis via synchronization algorithms, which both sides of a given link mutually share. Unique, link specific secrets eliminate the possibility that a single link being compromised could lead to the compromise of other links or an entire system.
Another benefit of such a ZKKM cryptographic solution, is that it avoids the complexity and processing latency overhead associated with PKI by eliminating the public key exchange and certificate processing. This advantage is realized by utilizing only symmetric cryptographic methods coupled with the capability to pre-calculate session keys in advance inside a secure device, which is never exposed outside of the security module, preferably within some form of physical tamper-resistant protection such as that found in a Hardware Security Module (HSM)/Trusted Execution Environment (TEE).
The processing and power consumption footprint of a ZKKM key management solution can be no greater than what is required for implementing a symmetric encryption like AES (e.g., which is well-known for its efficiency and low-overhead).
The aforementioned efficiency and low-overhead presumes the following two statements are true:
1) It must be a priority of the system architecture to select a digital signature cryptographic hash function that fits within the computational limits alluded to above.
2) An efficient symmetric algorithm (like AES) is selected for the bulk encryption.
Additional reduction in “real-time” processing overhead can be achieved by pre-calculating as much of the key management activities as possible, either as offline/background activities or between cryptographic sessions.
Finally, because there are no exposed shared secrets in a ZKKM system, the likelihood of a breach is further reduced over traditional PKI based systems.
Like this entry?
-
About the Entrant
- Name:Jon Shields
- Type of entry:teamTeam members:Jon ("Bart") Shields Jörg Huser Dave Gell
- Software used for this entry:Yes, Java, C/C++ on Automotive and IoT Hardware, as well as in Azure Cloud for Backend Server.
- Patent status:pending